Edge-to-Cloud Security
Overview
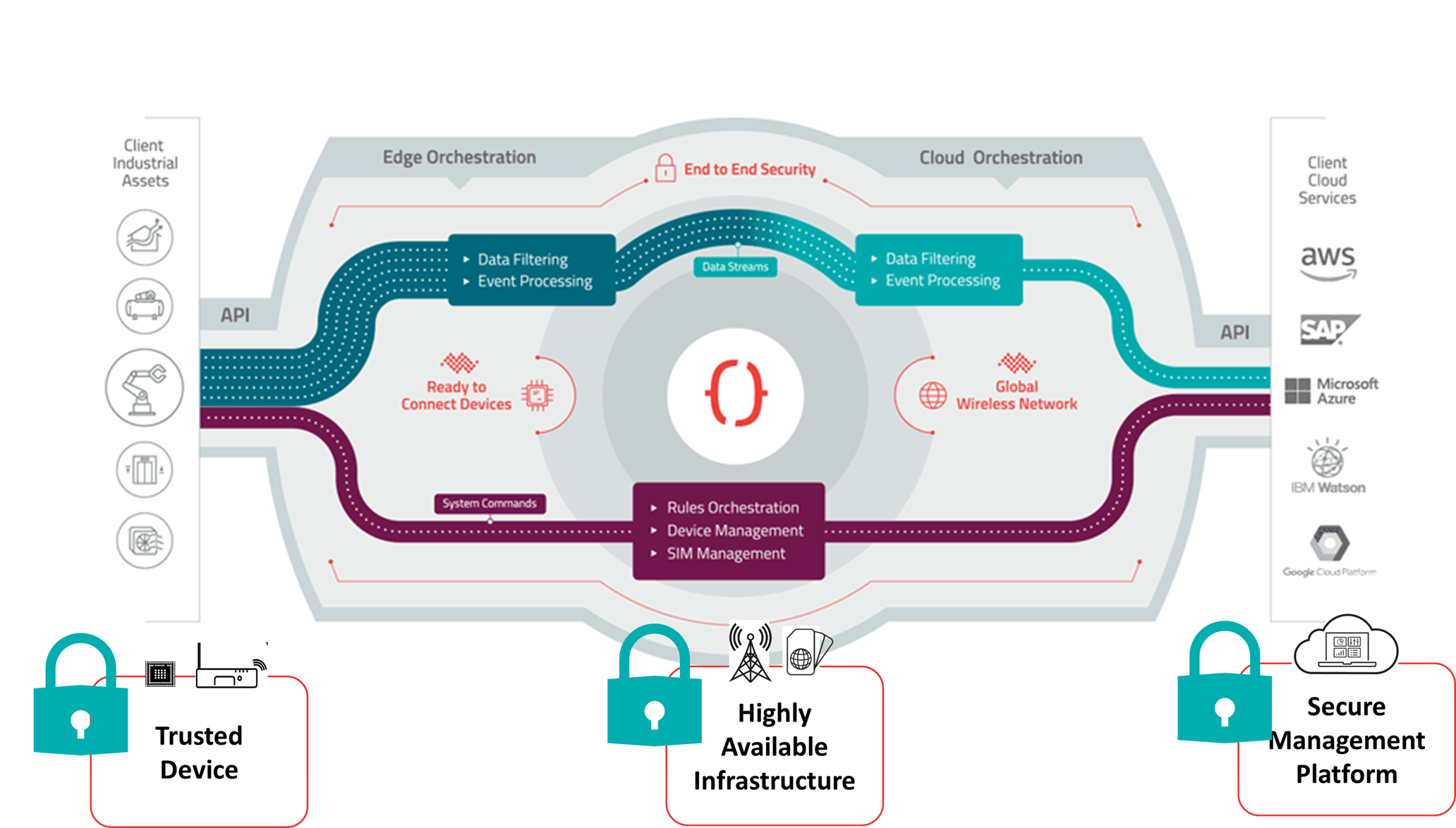
Octave provides end-to-end security that covers Octave edge devices, Octave's core infrastructure, and communications with external systems via Octave's Cloud REST APIs.
Key Security Features
Octave provides the following security features out of the box:
-
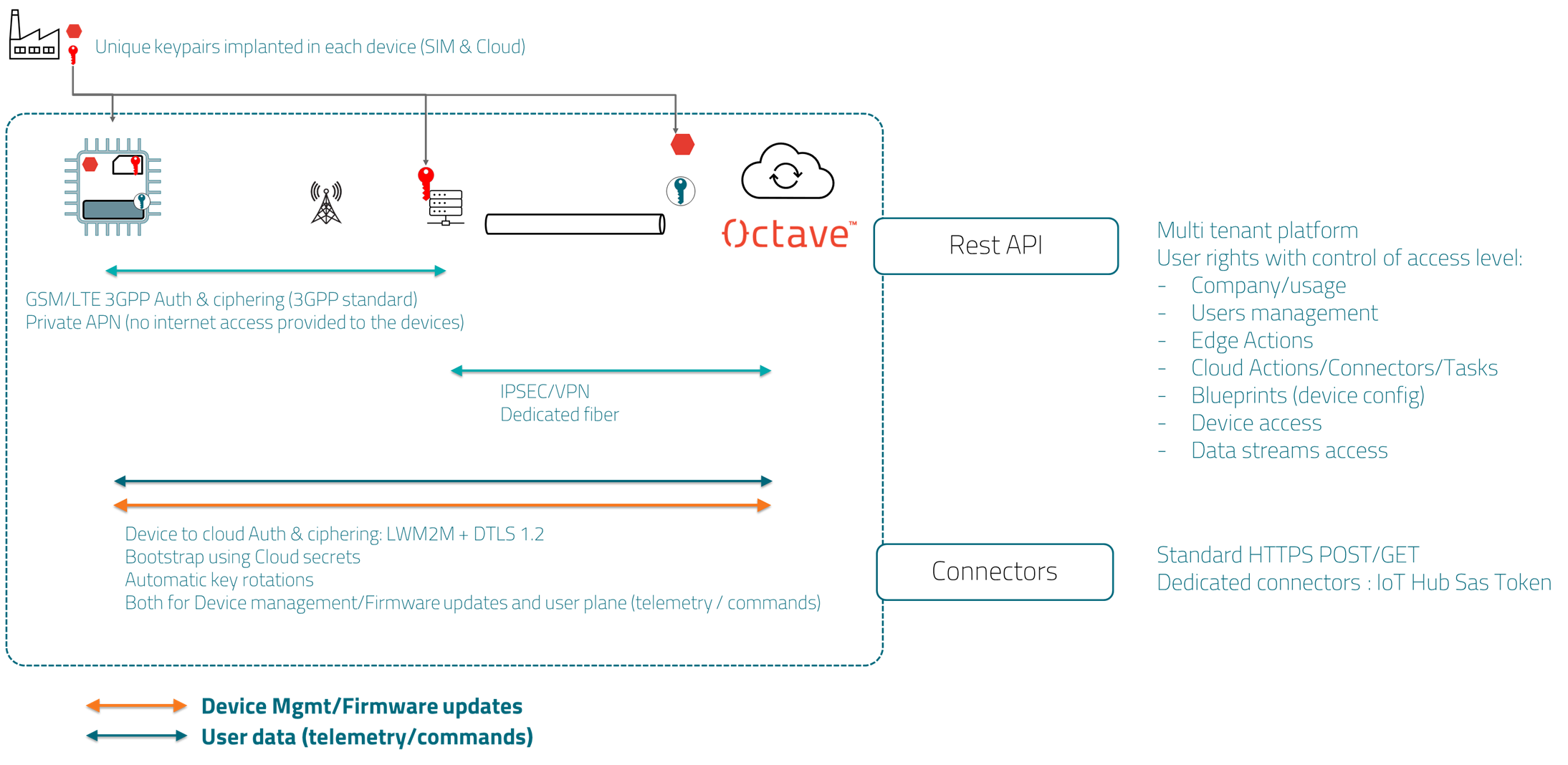
Zero-touch security provisioning:
- Factory-loaded secret keys (secure storage)
- SIM or integrated eSIM
- SIM and hardware mutual pairing
-
Secure boot and Secure firmware upgrade
-
Zero touch use of LWM2M + DTLS 1.2 Edge-to-Cloud protocol
-
Automated and Unlimited Key Rotations Over the air for Edge-to-Cloud Authentication
-
Cellular Network Authentication and Ciphering (3GPP Sim)
-
Private APN (cellular Access Point Name; Octave Devices do not have internet access)
-
Cloud-to-cloud Connectors Using Device Keys (Azure)
High level security diagram
Securing Octave Edge Devices
There are a number of steps required to prepare Octave edge devices for secure deployment. This includes securing the physical interfaces, root account, access to extended AT commands, and other aspects.
For Octave devices below version 3.4, we recommend you to follow the guidelines provided here
Octave 3.4 brings a number of key security feature enhancements:
- Signed firmware and Secure boot
- Device Access Control feature
Signed firmware and Secure boot
With a goal to always providing the best level of security without extra costs nor complex configurations on the customer side, Octave firmware 3.4.0 and above is fully signed, allowing the Octave Edge devices' Secure Boot to ensure the whole firmware stack is fully secure.
Octave devices which are shipped from the factory with version 3.4 and above will be secure by default, thus only accepting signed Octave firmware (3.4 and above).
Octave 3.4 signed firmware will install on non-secure hardware, although we strongly recommend customers to transition to 3.4 and enable the Secure Boot of their existing hardware which goes to production.
Device Access Control
With Device Access Control, you can control device SSH access via Octave's Resources and Blueprints.
Full documentation is here
Securing Cloud Access
User Permissions
Access to Octave is tightly controlled by Administrators who create and manage groups of users. These groups define what their members can access through a series of read/write settings which cover both the Octave Dashboard and Octave's Cloud REST APIs (discussed below).
For additional information see Managing User Groups and Permissions.
API Security
Octave's Cloud REST APIs allows you to programmatically invoke Octave's functionality. Octave provides API security by requiring each request header to include a master token and user name which are assigned to each user when the account is created.
You can find your master token and user name as described in Copying Your User Name and Master Token.
Updated about 3 years ago